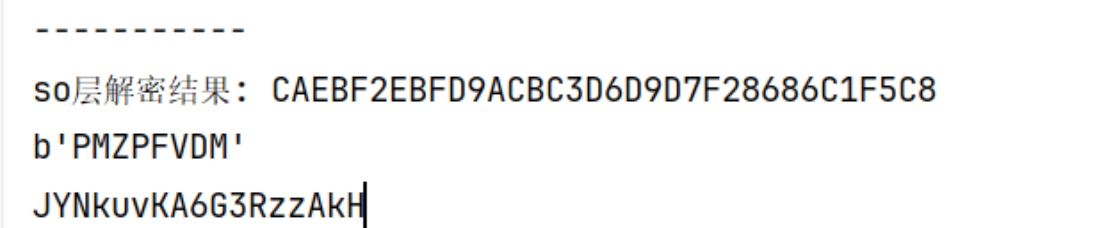
第九届“强网杯”行业领域专项赛车联网安全赛-初赛(CTF)WP
第九届“强网杯”行业领域专项赛车联网安全赛-初赛(CTF)WP
第九届“强网杯”行业领域专项赛车联网安全赛是由中央网信办、河南省人民政府指导,河南省委网信办、河南省教育厅、郑州市人民政府、信息工程大学、郑州大学、中国网络空间安全协会等单位联合主办的车联网安全专项赛事。车联网安全赛道线上CTF初赛旨在通过CTF解题,全面检验选手在智能网联汽车安全领域的实践能力。
强网-stop
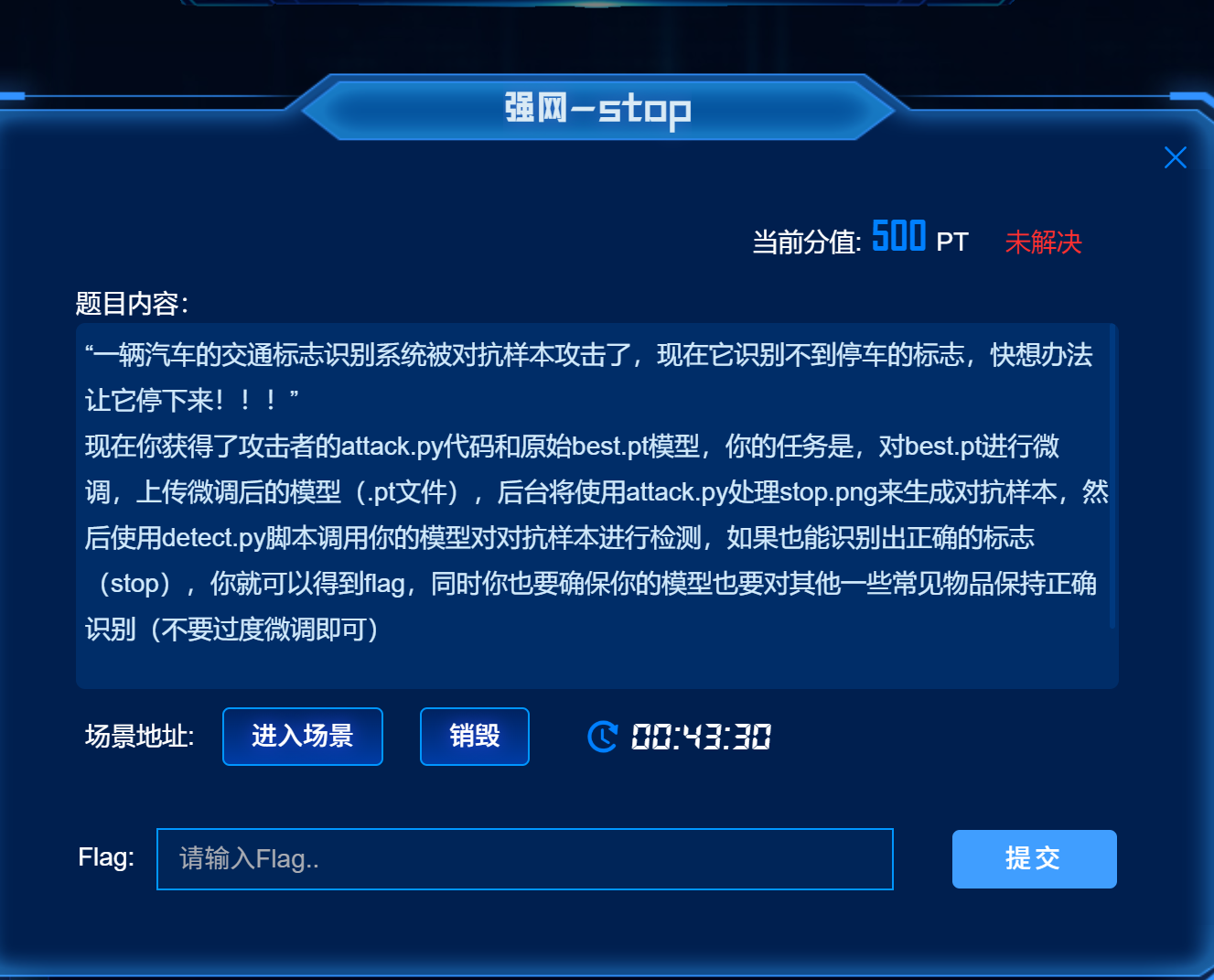
通过分析给出的代码,可以得到攻击本质是降低 stop sign 的 logits,那我们做防御策略就是增加 stop sign 的 logits(偏置+权重),即使被攻击降低,增加后的 logits 仍然足够高
策略1:增加偏置(Bias)
在分类层的输出层,直接增加 stop sign 类别的偏置:
1 | |
原理:
- 分类输出:
output = conv(features) + bias - 增加偏置 → 直接增加 logits → 提高 softmax 后的概率
优点:
- 简单直接,效果明显
- 不改变特征提取过程,对 other 类别影响小
策略2:增加权重(Weight)
同时增加 stop sign 对应通道的权重:
1 | |
原理:
- 增强 stop sign 特征在分类时的响应强度
- 使模型对 stop sign 相关特征更敏感
优点:
- 与偏置结合,双重保障
- 权重调整幅度小(10%),避免过度微调
微调策略:
只修改分类输出层,不影响特征提取
同时修改 3 个检测头,覆盖多尺度
调整幅度适中,既防御攻击又尽可能保持对其他类别的识别
所用脚本如下:
1 | |
运行后将生成的pt文件上传后得到flag
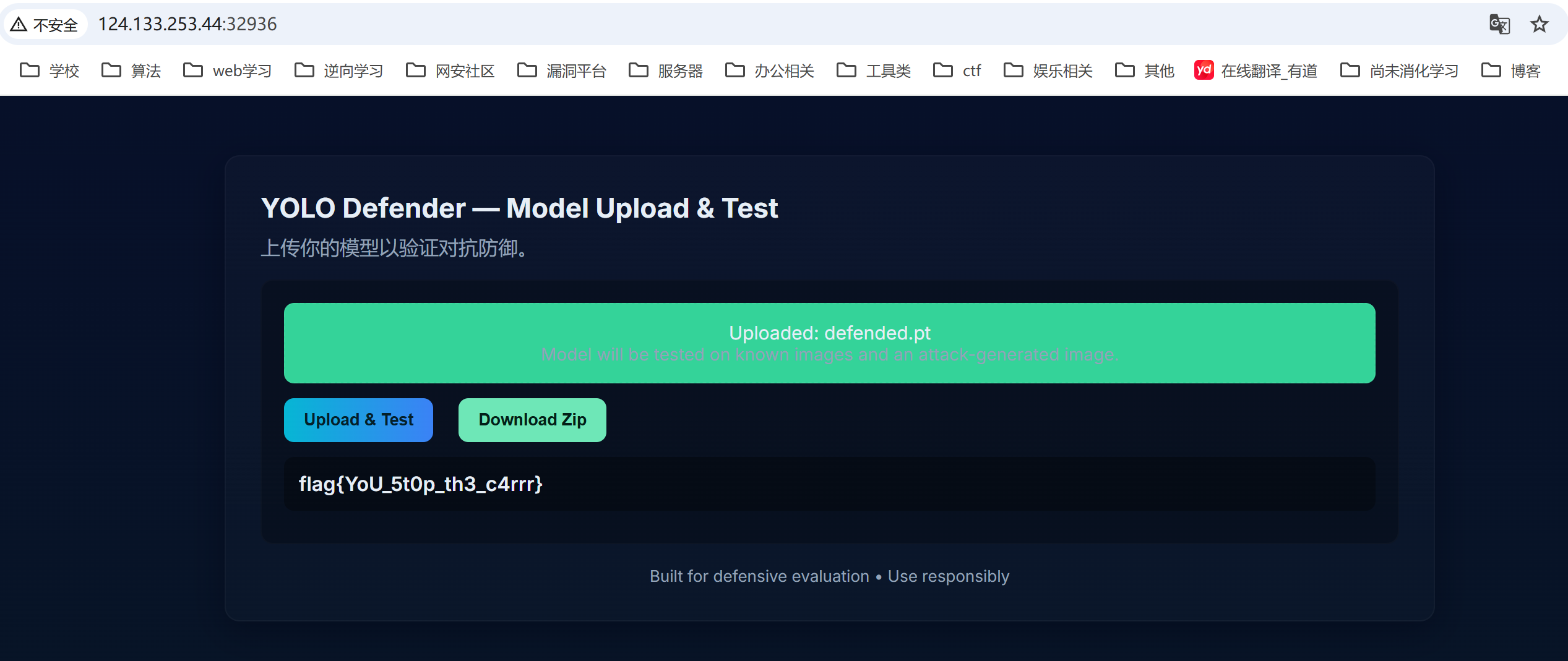
强网-SCAAES
题干如下:
1 | |
题目给了一个trs文件,我们可以用python的trsfile 库直接读取

大概思路如下:
- 泄露模型(Leakage Model):采用汉明重量(Hamming Weight, HW)。
- 针对 AES 第 1 轮 SBox 的中间值建立选择函数:
[ v_i(k) = S\big(p_i \oplus k\big) \quad\Rightarrow\quad L_i(k) = HW\big(v_i(k)\big) ]
其中 (p_i) 为第 (i) 条轨迹的第 (b) 个明文字节,(k) 为猜测的密钥字节。
- 针对 AES 第 1 轮 SBox 的中间值建立选择函数:
- 统计量:对每个时间采样点
t,计算L(k)与功耗T[:, t]的皮尔逊相关系数,取全时域的最大绝对相关值作为该k的评分:
[ \rho(k) = \max_t \big|\mathrm{corr}(L(k), T[:, t])\big| ] - 取最优猜测:对每个字节
b,取使得 (\rho(k)) 最大的k*作为该字节的估计。16 个字节拼接即为 128-bit 密钥。 - 大样本收敛:当轨迹数充足且对齐良好时,正确密钥对应的相关峰显著高于其他假设。
首先进行数据读取:
1 | |
然后进行侧信道攻击,下面给出精炼版 CPA 代码,默认使用 SBox 输出的 HW 泄露模型。
1 | |
注:上面将相关的所有时间点向量化一次算完,速度远快于逐点循环。若存在对齐抖动,可在 CPA 前做滑动窗口/降采样/高通滤波/动态时间规整等预处理。
在本题数据集上,使用上述流程复现得到的 16 字节密钥为:
1 | |
拼接为 32 位十六进制(大写):
1 | |
按题目格式输出即:flag{CCAEEED667CD6C04C7ABCCC26DC793F1}
强网-cancanneedflag
题目提供了以下附件:
canlog.txt- CAN总线日志文件(100306行)signal_map/signal_map.csv- 信号映射配置文件
signal_map.csv 结构:
该文件定义了信号到CAN消息的映射关系,包含以下字段:
signal: 信号名称(如speed, rpm, steer_angle, sig_1到sig_72等)can_id: CAN消息ID(16进制)byte: 数据在CAN消息中的字节位置len: 数据长度(字节数)type: 数据类型(uint8, uint16, int16等)
共有75个信号定义,其中sig_1到sig_72这72个信号很可能用于隐藏flag数据。
canlog.txt 格式:
CAN日志格式为:
1 | |
示例:
1 | |
步骤1:读取signal_map.csv,建立信号映射
1 | |
步骤2:解析canlog.txt,提取CAN消息
1 | |
步骤3:按照signal_map提取每个信号的值
1 | |
步骤4:按信号顺序提取最后一个值并转换为ASCII
1 | |
步骤5:提取flag
1 | |
完整解题脚本
1 | |
成功拿到flag:flag{V3h1cle_N3tw0rk1ng_53cu71ty}
强网-applet
解压文件发现是一个小程序的包,写一个代码来解析一下这个小程序
1 | |
会得到
然后去查看关键的这几个函数,没有格式化,但是不妨碍看
代码如下:
1 | |
就是一个RC4,解密就行:
1 | |
得到flag
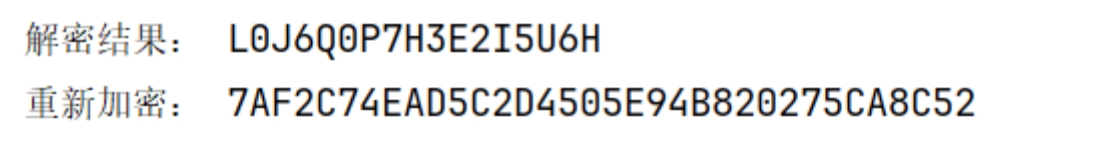
flag{L0J6Q0P7H3E2I5U6H}
强网vintelligence
给了一个流量包一个apk,首先分析流量包,得到了传输数据,需要分析apk来解密这段字符串,题目跟招商铸盾初赛的那一道vin交互很是相似
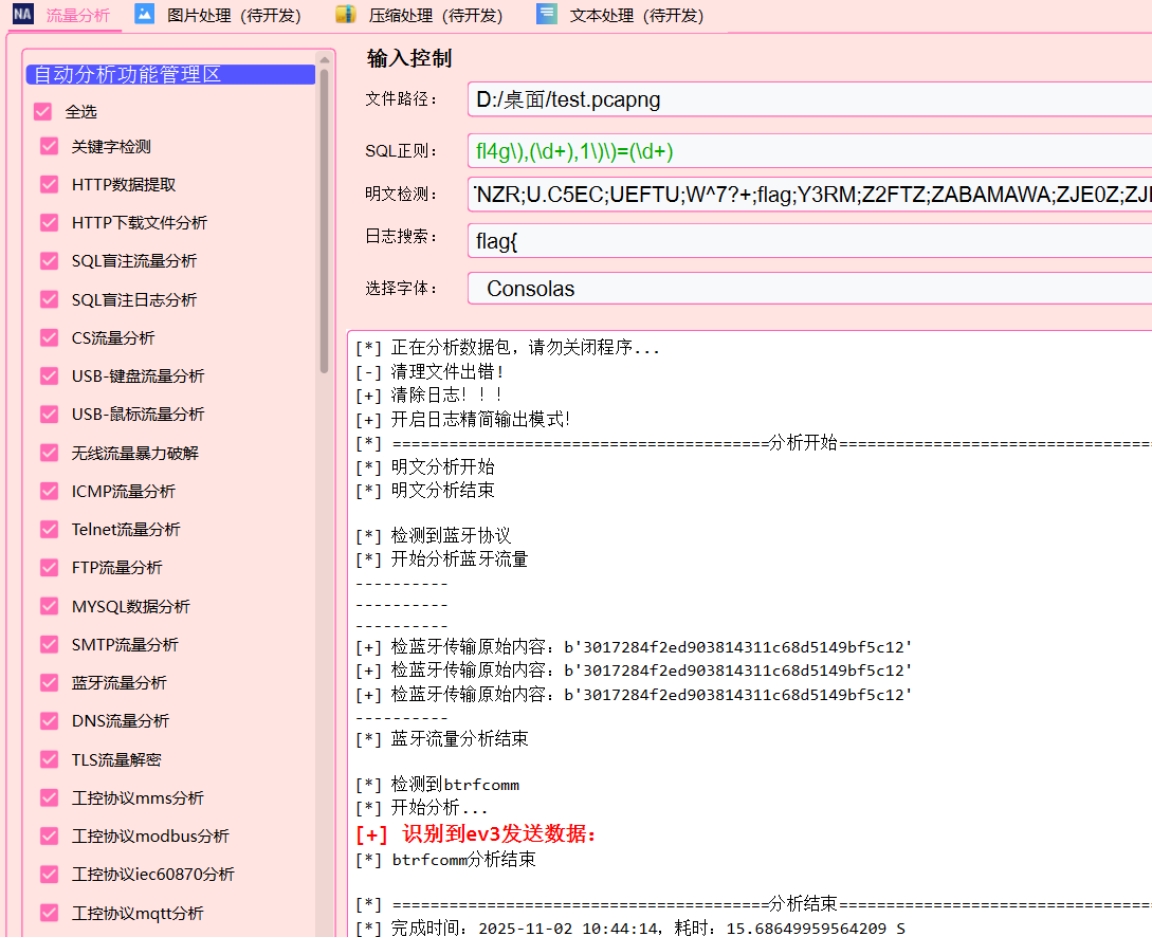
jadx打开文件,看到左边的类,有一个input
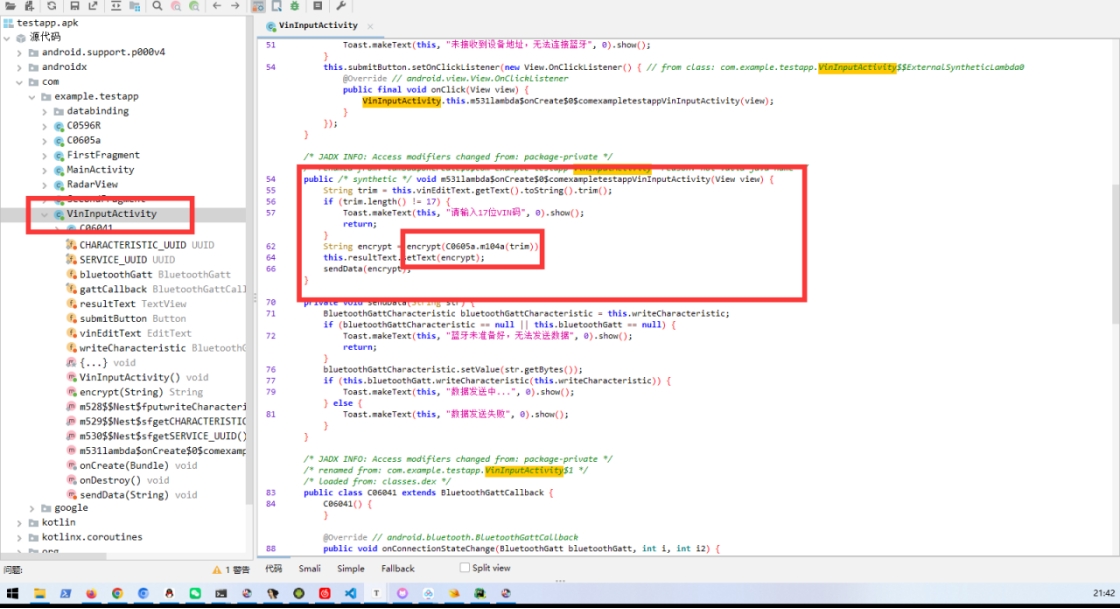
可以猜到就是一个java层加密一个so层加密

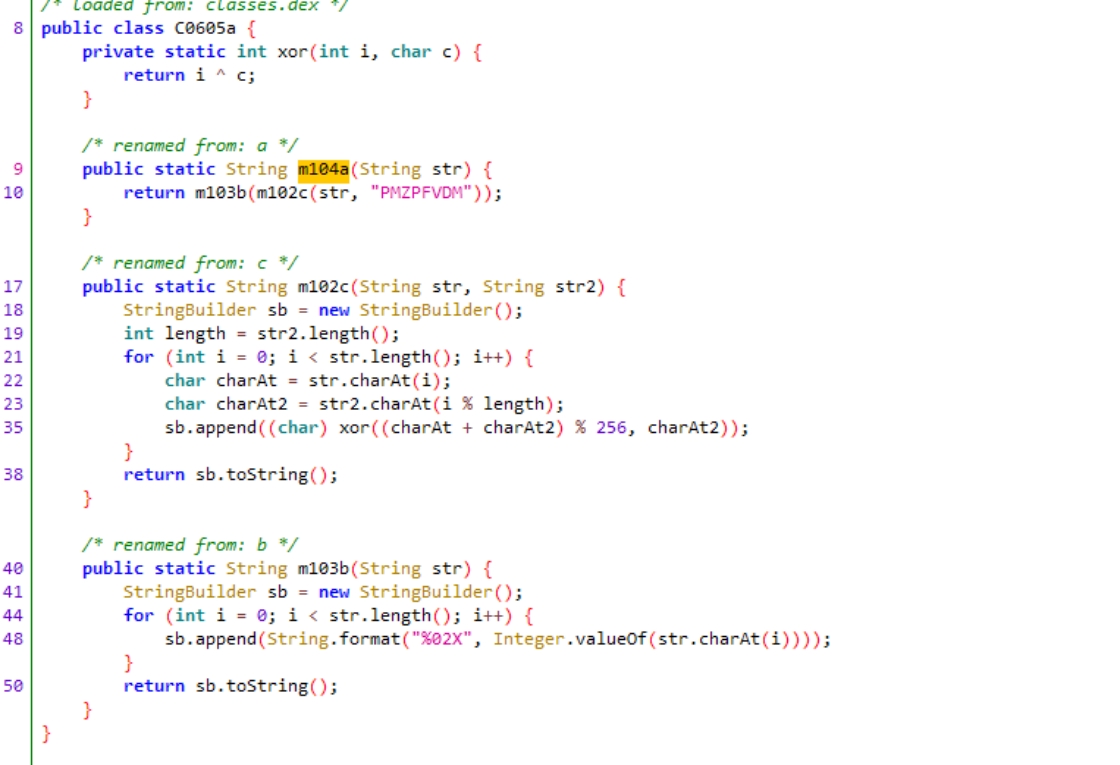
两个加密
java层的加密好写,就是一个c=(m+k)^k 的加密
解密直接m=(c-k)^k
1 | |
so层加密
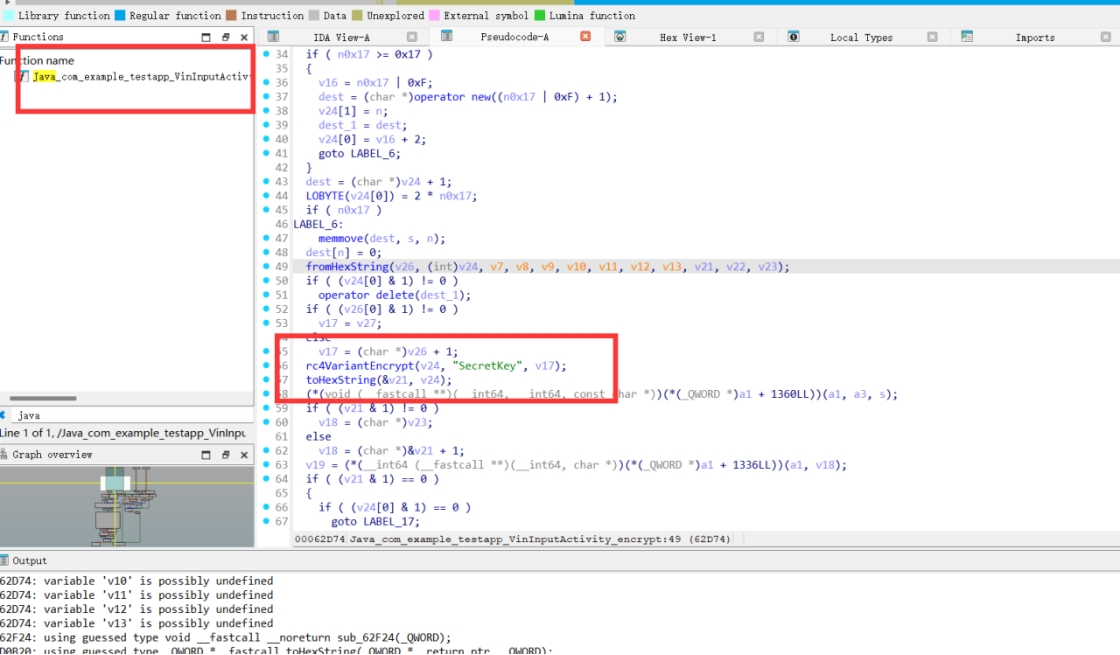
RC4加密
就是一个简单的小魔改
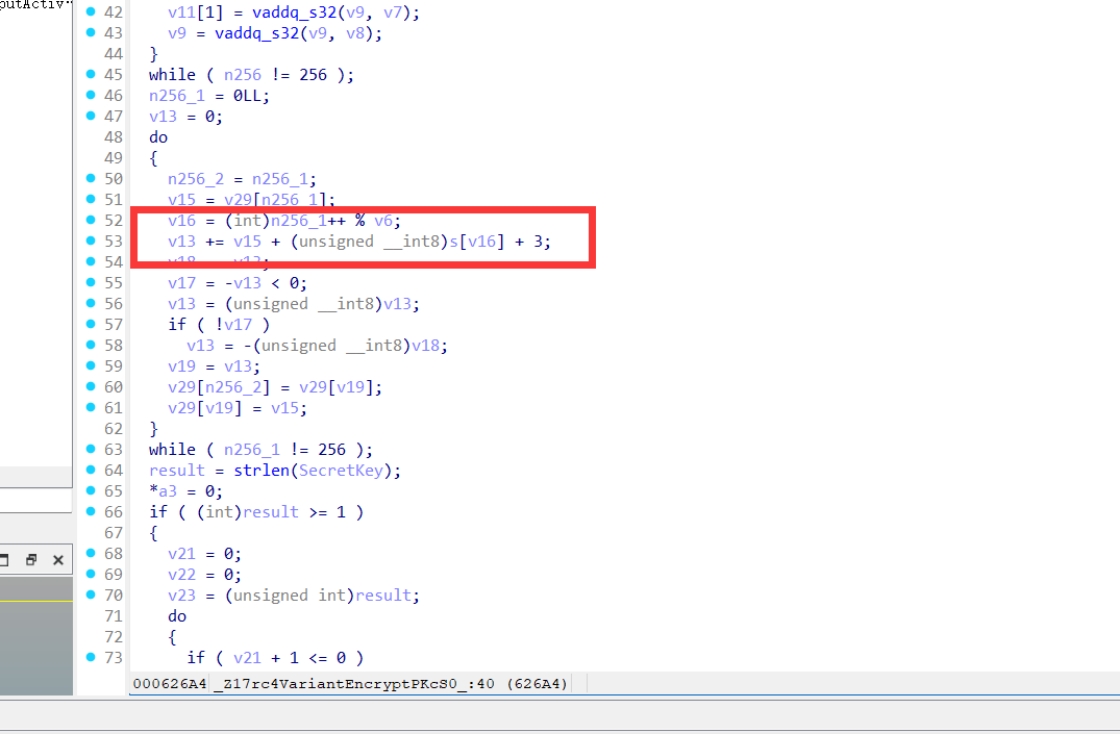
1 | |
注意一下输入就行,记得讲输入转换成字节
更简单的就是直接使用frida进行主动调用进行dump xor密钥流
我的主动调用,不过没有dump
1 | |
可以验证代码对错
总的解密代码:
1 | |
得到flag